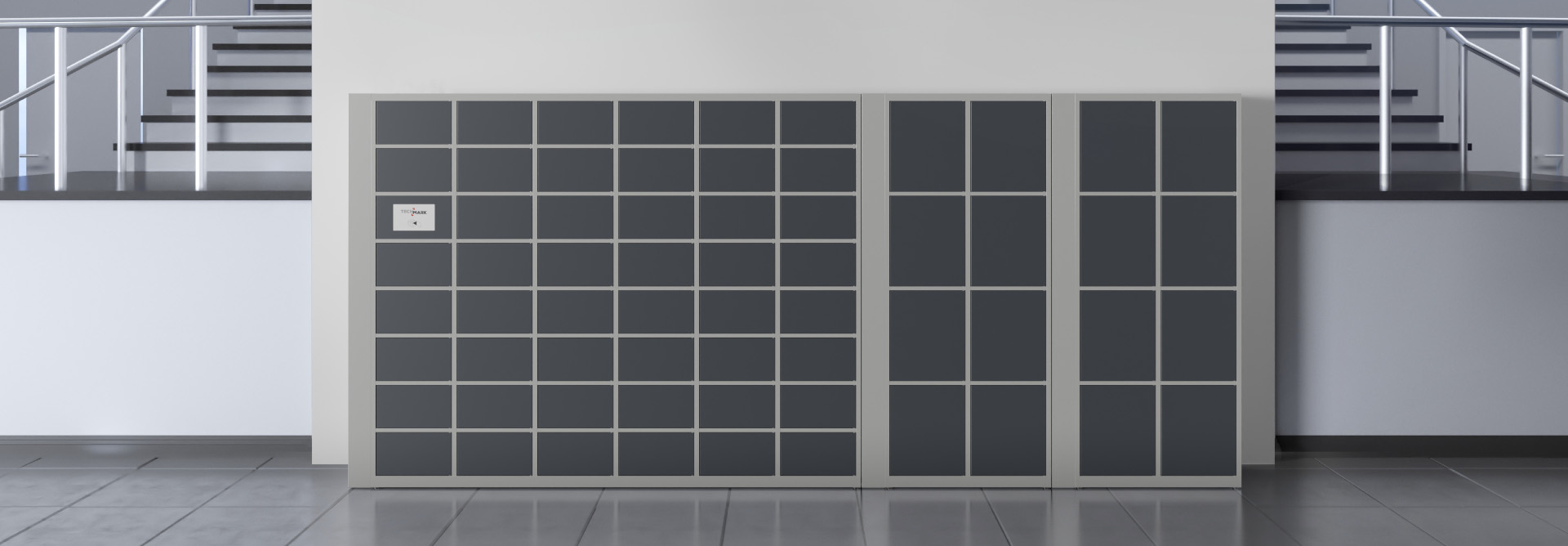
S.2.2 System
The S.2.2 System stands for TECHCODE RFID cabinets and cabinet sets with extensive capabilities, allowing remote management and administration, as well as support for numerous Users and their groups in multiple modes and schemes of operation.
The System features cabinets with up to 512 lockers.
The following can work in the S.2.2 System:
Clothing lockers
Multi-compartment cabinets
File cabinets with drawers

Access control and process automation are key characteristics of this system.
The S.2.2 system offers six modes to ensure the security of stored items, allowing access only to verified and known users. Each mode affects the functionality of the cabinet and the system.
The operating mode is selected by the Administrator, who can configure the various settings for the operation of the System and the cabinet, as well as the scope of users' rights.
The operating mode selected by the administrator affects the functionality and user rights.
Various methods are used for authorisation and identification, such as contactless cards, PIN codes or mobile phones.
The S.2.2 system also allows items to be defined and tracked in compartments.
System management can be carried out locally or remotely using network software. For this purpose, the cabinets have a built-in LAN interface (Ethernet or Wi-Fi).

System administrator (A)
The TECHCODE RFID system administrator has specific rights to manage the system and/or RFID cabinets.
Their responsibilities include entering data into the system, granting rights to users and managing RFID cabinets, such as remotely opening or releasing reserved cabinets and receiving information about failures.
Master user (M)
The System Administrator may grant Master rights to a defined System User, authorising them to perform the functions reserved for them.
The System Administrator can be assigned Master rights at the same time.
Defined user (U)
The basic user type of the TECHCODE RFID cabinet with System S.2.2 is the User defined in the System by the Administrator.
The administrator can add a user to the database by providing personal or identifying data, such as order number, position, department name, room number.
A user can also be assigned to a user group(s).
Undefined user (XY)
An undefined user, who has not been entered into the System by the Administrator, can use the TECHCODE RFID cabinet after fulfilling one of the conditions:
1. Assigning a personal access PIN,
2. Receiving access from another System User that has been previously defined.

Defining objects
The System Administrator defines objects by marking them with a special tag (e.g. NFC sticker, key ring, etc.) and enters them into the System. TECHCODE RFID cabinets can register the presence of defined assets in compartments by means of special readers.
Identification and authorisation
In order to grant access (authorisation) to a compartment or to perform a specific action in the S.2.2 System, it is necessary to correctly pass the identification process. Identification may concern:
1. user (defined or undefined in the System). The identification of the User can be carried out in different ways, e.g. by reading out specific identifiers, mobile phone or access data (login and password)
2. object - identification is carried out automatically by scanning the identifier, barcode or QR code assigned to the object.
ACCESS CONTROL
and process automation in S.2.2
with TECHCODE RFID cabinets

RFID cabinets operating in the S.2.2 system can be managed in two ways:
1. locally and autonomously via a touchscreen control panel,
2. remotely by means of management software S.2.2 running on a computer network.
The above management methods ensure encrypted communication.
- Selection of operating mode and configuration of cabinet parameters
- Division of cabinets into groups and definition of individual access rights for these groups
- Granting rights to specific users
- Remote opening/release of compartments in an emergency, e.g. if a card is lost or a PIN is forgotten, so that the administrator can open the compartment in question and allow the deposit to be taken.
The administrator has access to the following information:
- Alarms - detection and signalling of tamper alarm conditions. The alarm centre has a list of alarm events (e.g. burglary, tampering, etc.) recorded by the cabinet controller during the selected time period.
- Reports on actions performed by a specific user
- Reports on events recorded during a specific time period
- Reports on events concerning defined objects
- Cabinet occupancy - which cabinets are occupied/who is currently using a particular cabinet
- Event logs and system reports. Events from the Report Centre can be exported to a removable media connected to a USB port, the controller's internal memory or sent to an e-mail address.
Access to the TECHCODE RFID cabinet is possible for users who have undergone an identification and access authorisation process. This can be done in two ways:
1. Using a graphic touchscreen with built-in dual contactless reader with Mifare Ultralight/Classic/Plus/DESFire card support or EM125kHz card support and/or variable length PIN support (default 4-16 digits).
2. Using external readers, where identification can be performed using methods offered by specific devices

The TECHCODE RFID cabinet operating in the S.2.2 system has a touchscreen keypad and a built-in Mifare card reader.
It is supported by a variety of identification methods, including external readers that can replace or work in tandem with the built-in touch panel.
The scope of the User's rights and the type of activities performed by the User depend on:
- Cabinet operating mode previously selected by the Administrator
- The settings configured by the Administrator for individual cabinet parameters and functions, such as how and where to identify the User (e.g. which reader will handle the User's card)
- Individual rights granted to the User by the Administrator (e.g. possibility of choosing a compartment, etc.).
The database is stored in a secure disk storage location. No access from other applications or from an external user, etc.
The database can also be exported to an external USB drive.
Cabinets that can operate in this system

These cabinets are also known as the following cabinets:
- Deposit
- Breakfast
- Clean clothing

Lockers are used to store clothes and other items in staff changing rooms, hotels, hospitals and sports facilities.

They serve to securely store all types of documents (office, accounting, personal, etc.) in standardised formats.
The TECHCODE RFID cabinet operating in the S.2.2 System can operate in one of six Operating Modes, which is selected and activated by the Administrator prior to its first use. The selection of a particular Operating Mode determines the Schemes and functions that the cabinet will perform, as well as the information that will be displayed on the cabinet's monitor.
S.2.2 system - Operating mode 1 - operating scheme 1: U/1A (*)
The administrator defines the user and how they will identify themselves in the system and permanently assigns one compartment to them.
The assigned compartment is marked as occupied and is not taken into account when allocating further free compartments.
The system identifies the user by means of an assigned verification method, e.g. identifier, mobile phone, PIN or biometric data, and authorises access to the cabinet.
After successful authorisation, a single compartment, previously assigned by the administrator to a user defined in the system, is automatically opened.
A compartment may be used repeatedly by the user until the user's identifier is returned or the authorisation to open the compartment is withdrawn by the administrator.
S.2.2 system - Operating mode 2 - operating scheme 1: U/1A (*)
The administrator defines the user and how they will identify themselves in the system and permanently assigns one compartment to them.
The assigned compartment is marked as occupied and is not taken into account when allocating further free compartments.
The system identifies the user by means of an assigned verification method, e.g. identifier, mobile phone, PIN or biometric data, and authorises access to the cabinet.
After successful authorisation, a single compartment, previously assigned by the administrator to a user defined in the system, is automatically opened.
A compartment may be used repeatedly by the user until the user's identifier is returned or the authorisation to open the compartment is withdrawn by the administrator.
S.2.2 system - Operating mode 2 - operating scheme 2: U/1S (*)
The administrator defines the user and how they will be identified in the system
The system identifies the user by means of an assigned verification method, e.g. identifier, mobile phone, PIN or biometric data, and authorises access to the cabinet.
After successful authorisation, the system searches for and automatically opens the first free compartment in which the user deposits an item. The system assigns this compartment to the user.
Each time the user is identified and authorised again, the system automatically opens the compartment assigned to the user.
The compartment is assigned to the user until the user's identifier is returned or the authorisation to open the compartment is revoked by the administrator.
S.2.2 system - Operating mode 2 - operating scheme 3: U/123S (*)
The administrator shall create a compartment group(s). Each group may consist of max. 32 compartments.
The administrator defines the user and assigns the method used to identify the user in the system.
The system identifies the user by means of an assigned verification method, e.g. identifier, mobile phone, PIN or biometric data, and authorises access to the cabinet.
After successful authorisation, the system automatically opens the first free compartment from the group previously created by the administrator, in which the user is depositing something. The system assigns this compartment to the user. Each time the user is identified and authorised again, the system automatically opens the compartment assigned to the user.
The compartment is assigned to the user until the user's identifier is returned or the authorisation to open the compartment is revoked by the administrator.
S.2.2 system - Operating mode 3 - operating scheme 1: UUU/1A (*)
The administrator defines the users and how they will be identified in the system and permanently assigns one compartment to them.
The assigned compartment is marked as occupied and is not taken into account when allocating further free compartments.
The system identifies the users by means of an assigned verification method, e.g. identifier, mobile phone, PIN or biometric data, and authorises access to the cabinet.
After successful authorisation, one compartment is automatically opened, assigned by the administrator to the user group to which the user identified by the system belongs.
The assigned compartment can be used alternately by users until their identifiers are returned or their authorisation to open it is revoked by the administrator.
S.2.2 system - Operating mode 4 - operating scheme 1: U/1S (*)
The administrator defines the user and how they will be identified in the system.
The system identifies the user by means of an assigned verification method, e.g. identifier, mobile phone, PIN or biometric data, and authorises access to the cabinet.
After positive authorisation, the system searches for and automatically opens the first compartment in which an item is deposited.
The user retrieves a resource from the compartment and closes the compartment.
Once the user has been identified and authorised again, the system automatically opens the first free compartment in which the user can deposit the previously retrieved item.
S.2.2 system - Operating mode 4 - operating scheme 2: U/123U (*)
The administrator defines the user and how they will be identified in the system.
The administrator creates a group / groups of compartments and assigns them to a defined user who will be able to use them. Each group can consist of up to 32 compartments.
The system identifies the user by means of an assigned verification method, e.g. identifier, mobile phone, PIN or biometric data, and authorises access to the cabinet.
After successful authorisation, the user selects one compartment from the group of compartments provided, which the system opens. The user retrieves the resource deposited in the compartment and closes the compartment.
Once the user has been identified and authorised again, the system automatically opens the first free compartment in which the user can deposit the previously retrieved item.
S.2.2 system - Operating mode 4 - operating scheme 3: UUU/123U (*)
The administrator defines the users and how they will be identified in the system.
The administrator creates a group / groups of compartments and assigns them to defined users who will be able to use them.
Each group can consist of up to 32 compartments.
The system identifies the users by means of an assigned verification method, e.g. identifier, mobile phone, PIN or biometric data, and authorises access to the cabinet.
After successful authorisation, the user selects one compartment from the group of compartments provided, which the system opens. The user retrieves the resource deposited in the compartment and closes the compartment.
Once the user has been identified and authorised again, the system automatically opens the first free compartment in which the user can deposit the previously retrieved item.
S.2.2 system - Operating mode 5 - operating scheme 1: U/1A (*)
The administrator defines the user and how they will identify themselves in the system and permanently assigns one compartment to them.
The assigned compartment is marked as occupied and is not taken into account when allocating further free compartments.
The system identifies the user by means of an assigned verification method, e.g. identifier, mobile phone, PIN or biometric data, and authorises access to the cabinet.
After successful authorisation, a single compartment, previously assigned by the administrator to a user defined in the system, is automatically opened.
A compartment may be used repeatedly by the user until the user's identifier is returned or the authorisation to open the compartment is withdrawn by the administrator.
S.2.2 system - Operating mode 5 - operating scheme 2: XYPIN/123XY
by an undefined user
An undefined user selects one of the free compartments provided by the system. The selected compartment opens so that the user can deposit something therein.

PIN code
When the compartment is closed, an undefined user assigns the PIN code needed to reopen it. The compartment is marked as occupied in the system.
The system identifies the user by means of an assigned verification method, e.g. identifier, mobile phone, PIN or biometric data, and authorises access to the cabinet.
Po odebraniu przez niezdefiniowanego użytkownika depozytu i zamknięciu skrytki, przypisany do niej kod PIN wygasa, a skrytka zostaje oznaczona w systemie jako wolna.
S.2.2 system - Operating mode 5 - operating scheme 3: XYPIN/1S (*)
An undefined user selects one of the free compartments provided by the system. The selected compartment opens so that the user can deposit something therein.

PIN code
When the compartment is closed, an undefined user assigns the PIN code needed to reopen it and collect the deposited items. The compartment is marked as occupied in the system.
The system identifies the user and provides authorisation to open the compartment once based on a PIN code previously assigned by the user.
When an undefined user collects a deposit and closes the compartment, the PIN assigned thereto expires and the compartment is marked as free in the system.
S.2.2 system - Operating mode 5 - operating scheme 4: XYPIN/123S
The administrator creates a compartment group. Each group can consist of up to 32 compartments. The system selects from the created group and opens the first free compartment in which an undefined user can deposit something.

PIN code
When a compartment is closed, an undefined user assigns a PIN code, which is needed to reopen the compartment and take a deposit from it. The compartment is marked as occupied in the system.
The system identifies the user and provides authorisation to open the compartment once based on a PIN code previously assigned by the user.
When an undefined user collects a deposit and closes the compartment, the one-time PIN assigned thereto expires and the compartment is automatically marked as free in the system.
S.2.2 system - Operating mode 6 - operating scheme 1: U/1A (*)
The administrator defines the user and how they will identify themselves in the system and permanently assigns one compartment to them.
The assigned compartment is marked as occupied and is not taken into account when allocating further free compartments.
The system identifies the user by means of an assigned verification method, e.g. identifier, mobile phone, PIN or biometric data, and authorises access to the cabinet.
to a single user
After successful authorisation, a single compartment, previously assigned by the administrator to a user defined in the system, is automatically opened.
A compartment may be used repeatedly by the user until the user's identifier is returned or the authorisation to open the compartment is withdrawn by the administrator.
S.2.2 system - Operating mode 6 - operating scheme 2: UUU/1A
The administrator defines the users, assigns a single compartment to them and how they will be identified by the system, e.g. by means of:
• PIN code (same for all or different for each)
• Identifiers
The system identifies and authorises the one-time opening of the compartment to the first user who correctly identifies themselves by PIN or card.
Following positive authorisation, the assigned compartment is automatically opened. The system identifies which card/PIN code opened the compartment.
When a compartment is closed, it is automatically marked as free in the system. The system automatically deactivates all granted authorisations to reopen this compartment.
S.2.2 system - Operating mode 6 - operating scheme 3: M/UPIN/1S
A Master user deposits the item in the first free compartment selected by the system.
Selects from a list of users predefined by the administrator to whom the system sends by email the one-time access code (PIN) assigned by the Master user to open the compartment.
The system identifies the defined user and authorises them to open the compartment once based on a PIN code.
Upon positive authorisation, the compartment is automatically opened.
Once the deposit is collected by the defined user and the compartment is closed, the one-time PIN assigned thereto expires. The compartment is automatically marked as free in the system.
S.2.2 system - Operating mode 6 - operating scheme 4: M/UPIN/1M
A Master user deposits the item in a compartment of their choice.
Selects from a list of users predefined by the administrator to whom the system sends by email the one-time access code (PIN) assigned by the Master user to open the compartment.
The system identifies the defined user and authorises them to open the compartment once based on a PIN code.
Upon positive authorisation, the compartment is automatically opened.
Once the deposit is collected by the defined user and the compartment is closed, the one-time PIN assigned thereto expires.
The compartment is automatically marked as free in the system.
S.2.2 system - Operating mode 6 - operating scheme 5: M/XYPIN/1M
A Master user scans a barcode, QR code into the system or assigns a PIN code to the deposit itself.
He selects the compartment in which he deposits the item, transmits the data needed to open the compartment to an undefined user outside the system (e.g. by email, SMS, telephone, etc.).
The system identifies the undefined user and authorises them to open the compartment once, based on the data provided to them by the Master user.
Upon positive authorisation, the compartment is automatically opened.
Once the deposit is collected by an undefined user and the compartment is closed, the one-time access data assigned thereto expires.
The compartment is automatically marked as free in the system.

